First, let's get a few things out of the way.
- This has nothing to do with virtual machines. This blog is about backing up a physical computer.
- I'll be using Veeam Backup & Replication 11 (Build 11.0.1.1261) P20220302 and Ubuntu server 22.04.1 LTS. Veeam in this version does not officially support Ubuntu 22.10. This complicates things a little, as you will see, but it works.
- I will focus on the Linux backup and bare-metal restore part. For all intents and purposes, it does not matter, if you use the standalone Veeam agent for Linux or the full VBR product. It does not matter, if you store the backup locally or on a remote repository. In this blog, I will use Veeam Backup & Replication Community Edition and store the backup in a remote repository.
- There is some command line (shell) work required, but don't worry. It is mostly copy & paste.
- You should already know how to work with Veeam in general. I will focus mostly on the parts the pertain to LUKS encryption and bare-metal restore.
- I will use the server version of Ubuntu but it works the same way with the desktop version.
Part 1 - Installing Veeam agent for Linux
Saving the operating system disk device name in a variable
Understanding the disk layout
- /dev/sda1 is the EFI system partition (ESP) and is mounted as /boot/efi.
- /dev/sda2 is the boot partiton and is mounted as /boot.
- /dev/sda3 is where it's at. This partition is the encrypted LUKS container. Inside the container, there is the LVM with a volume group ubuntu--vg and inside there is a logical volume ubuntu--lv.
- Also, note there are two mapper devices, dm_crypt-0 and ubuntu--vg-ubuntu--lv. dm_crypt-0 is the LUKS container and ubuntu--vg-ubuntu--lv is the opened LVM volume group which is mounted as /.
Filesystem Size Used Avail Use% Mounted on
control dm_crypt-0 ubuntu--vg-ubuntu--lv
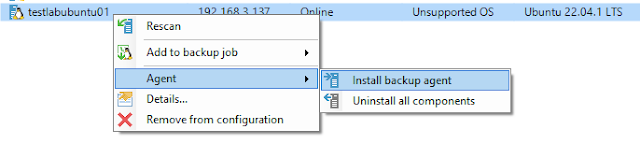
Installing Veeam agent for Linux
Issues with installing Veeam agent for Linux on Ubuntu 22.04 or later host
Updating the system
From here on, I largely follow the official guide but like I wrote, installation will fail, so you need to change a few things.
Adding Veeam repository
Download the Veeam repository Debian Software Package. Veeam would have you sign up and create an account in order to get this file, but you can simply click on the link and you won't need to be logged in. You can find the latest version here without login. Or you can enter this command:
wget https://repository.veeam.com/backup/linux/agent/dpkg/debian/public/pool/veeam/v/veeam-release-deb/veeam-release-deb_1.0.8_amd64.deb
Add the Veeam repository.
sudo dpkg -i ./veeam-release* && apt-get update
You might get an error like this, but it can be safely ignored.
W: Problem unlinking the file /var/cache/apt/pkgcache.bin - RemoveCaches (13: Permission denied)
W: Problem unlinking the file /var/cache/apt/srcpkgcache.bin - RemoveCaches (13: Permission denied)
Optionally, you can verify that the repository is installed
admin01@testlabubuntu01:~$ grep veeam /etc/apt/sources.list /etc/apt/sources.list.d/*
/etc/apt/sources.list.d/veeam.list:deb [arch=amd64] http://repository.veeam.com/backup/linux/agent/dpkg/debian/public stable veeam
admin01@testlabubuntu01:~$
Update the repository
sudo apt update
Starting the Veeam agent for Linux installation
- A signed (pre) bootloader (shim) is installed
- You have a Machine Owner Key (MOK) certificate
- the MOK certificate is installed with shim
- the Veeam kernel module is signed with the MOK certificate
Machine Owner Key (MOK) certificate enrollment
Confirm the password.
When you are back on the prompt, the agent installation is finished. However, this does not take care of everything. You may notice, that the MOK certificate is still not enrolled but it is scheduled for enrollment.
modprobe: ERROR: could not insert 'veeamsnap': Operation not permitted
admin01@testlabubuntu01:~$
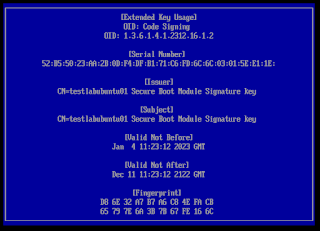
Optionally, you can view the key before you enroll it. It is a self-signed certificate for signing kernel modules (code signing) that Ubuntu generated for you.
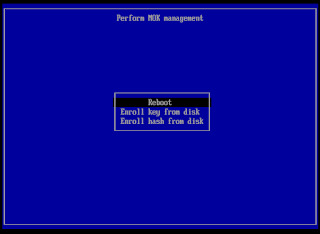
Back on the [Enroll MOK] screen (see screenshot above), choose "Continue". Answer "Enroll the key(s)?" with yes.
You may see this screen and may have to select the key (there should only be one key), but I did not get this screen every time during my testing.
Enter the password that you chose during the installation of Veeam agent for Linux. This password, as I understand it, is needed only for the enrollment of the MOK certificate and is then not needed any longer.














No comments:
Post a Comment